Get Xmlrpc Wordpress Exploit Background
This password guessing attack may also be faster, with the result being you can attempt more passwords. Wordfence scan leverages the same proprietary feed, alerting you quickly about security issues or if your site is compromised. In affected versions the widgets editor introduced in wordpress 5.8 beta 1 has improper handling of html input in the custom html feature. The wordpress security plugin provides the best protection available for your website. It is also recommended on some forums to check for the existence of an option via code:
For Only $9 You can get UNLIMTED Updates & Downloads to 3400+ Wordpress Themes and Plugins. Check it Out at DOWN47.COM
 WordPress XML-RPC Pingback Vulnerability - AVsecurity from www.avsecurity.in You could also use burp or your favorite scripting language for this request. A broken plugin allows it to be changed; Although it is now largely being replaced by the rest api released by wordpress, it is still used for backward compatibility. "true if option value has changed, false if not or if update failed. Powered by the constantly updated threat defense feed, wordfence firewall stops you from getting hacked. In affected versions the widgets editor introduced in wordpress 5.8 beta 1 has improper handling of html input in the custom html feature. ,bilal rizwan here hope your doing great & having fun learning from the community like i am. What is this post about ?
WordPress XML-RPC Pingback Vulnerability - AVsecurity from www.avsecurity.in You could also use burp or your favorite scripting language for this request. A broken plugin allows it to be changed; Although it is now largely being replaced by the rest api released by wordpress, it is still used for backward compatibility. "true if option value has changed, false if not or if update failed. Powered by the constantly updated threat defense feed, wordfence firewall stops you from getting hacked. In affected versions the widgets editor introduced in wordpress 5.8 beta 1 has improper handling of html input in the custom html feature. ,bilal rizwan here hope your doing great & having fun learning from the community like i am. What is this post about ?
This leads to stored xss in the custom html widget. This has been patched in. You could also use burp or your favorite scripting language for this request. The vulnerability is more of a spam menace than traditional malware, but gives search engines enough reason to block the site on accusations of distributing spam. This password guessing attack may also be faster, with the result being you can attempt more passwords. A broken plugin allows it to be changed; Database hacking is among the most important arts of the hacker. It is also recommended on some forums to check for the existence of an option via code: Wordfence scan leverages the same proprietary feed, alerting you quickly about security issues or if your site is compromised. The wordpress security plugin provides the best protection available for your website. In affected versions the widgets editor introduced in wordpress 5.8 beta 1 has improper handling of html input in the custom html feature. According to the wordpress codex (and my experiences developing with wp) note an important subtlety in the return value here: Apr 26, 2018 · 4 min read.
What is this post about ? A hacker has broken into redis/apc/memcached and modified the cache; A hacker manages to change the title via an exploit; In affected versions the widgets editor introduced in wordpress 5.8 beta 1 has improper handling of html input in the custom html feature. The vulnerability is more of a spam menace than traditional malware, but gives search engines enough reason to block the site on accusations of distributing spam.
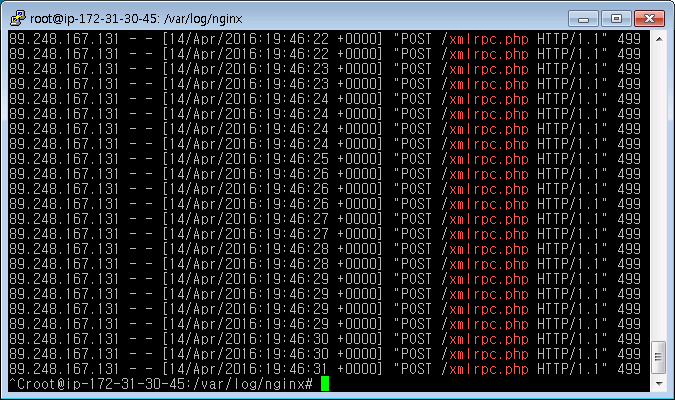 WordPress xmlrpc.php DDOS / exploit / 공격 과 대처 방법 - GRIP.News from grip.news A compromised plugin uses a filter to change the title; A hacker has broken into redis/apc/memcached and modified the cache; File based caches have been compromised; Although it is now largely being replaced by the rest api released by wordpress, it is still used for backward compatibility. Usually, the hacker is seeking access to data and obviously, the database is usually where it resides. The wordpress security plugin provides the best protection available for your website. Database hacking is among the most important arts of the hacker. A broken plugin allows it to be changed;
WordPress xmlrpc.php DDOS / exploit / 공격 과 대처 방법 - GRIP.News from grip.news A compromised plugin uses a filter to change the title; A hacker has broken into redis/apc/memcached and modified the cache; File based caches have been compromised; Although it is now largely being replaced by the rest api released by wordpress, it is still used for backward compatibility. Usually, the hacker is seeking access to data and obviously, the database is usually where it resides. The wordpress security plugin provides the best protection available for your website. Database hacking is among the most important arts of the hacker. A broken plugin allows it to be changed;
It is also recommended on some forums to check for the existence of an option via code: You could also use burp or your favorite scripting language for this request. Database hacking is among the most important arts of the hacker. The vulnerability is more of a spam menace than traditional malware, but gives search engines enough reason to block the site on accusations of distributing spam. This leads to stored xss in the custom html widget. Apr 26, 2018 · 4 min read. In affected versions the widgets editor introduced in wordpress 5.8 beta 1 has improper handling of html input in the custom html feature. A broken plugin allows it to be changed; A compromised plugin uses a filter to change the title; A hacker has broken into redis/apc/memcached and modified the cache; The wordpress security plugin provides the best protection available for your website. What is this post about ? This has been patched in.
It is also recommended on some forums to check for the existence of an option via code: This leads to stored xss in the custom html widget. A hacker has broken into redis/apc/memcached and modified the cache; Database hacking is among the most important arts of the hacker. Wordfence scan leverages the same proprietary feed, alerting you quickly about security issues or if your site is compromised.
 Disable XML RPC WordPress - how to disable xml-rpc in wordpress 3 from dieci-csinalt.com Wordfence scan leverages the same proprietary feed, alerting you quickly about security issues or if your site is compromised. File based caches have been compromised; A compromised plugin uses a filter to change the title; It is also recommended on some forums to check for the existence of an option via code: What is this post about ? Database hacking is among the most important arts of the hacker. This leads to stored xss in the custom html widget. A hacker has broken into redis/apc/memcached and modified the cache;
Disable XML RPC WordPress - how to disable xml-rpc in wordpress 3 from dieci-csinalt.com Wordfence scan leverages the same proprietary feed, alerting you quickly about security issues or if your site is compromised. File based caches have been compromised; A compromised plugin uses a filter to change the title; It is also recommended on some forums to check for the existence of an option via code: What is this post about ? Database hacking is among the most important arts of the hacker. This leads to stored xss in the custom html widget. A hacker has broken into redis/apc/memcached and modified the cache;
What is this post about ? Powered by the constantly updated threat defense feed, wordfence firewall stops you from getting hacked. A hacker has broken into redis/apc/memcached and modified the cache; This password guessing attack may also be faster, with the result being you can attempt more passwords. Usually, the hacker is seeking access to data and obviously, the database is usually where it resides. According to the wordpress codex (and my experiences developing with wp) note an important subtlety in the return value here: "true if option value has changed, false if not or if update failed. This has been patched in. A broken plugin allows it to be changed; ,bilal rizwan here hope your doing great & having fun learning from the community like i am. Wordfence scan leverages the same proprietary feed, alerting you quickly about security issues or if your site is compromised. In affected versions the widgets editor introduced in wordpress 5.8 beta 1 has improper handling of html input in the custom html feature. It is also recommended on some forums to check for the existence of an option via code:
Get Xmlrpc Wordpress Exploit Background. "true if option value has changed, false if not or if update failed. The wordpress security plugin provides the best protection available for your website. The vulnerability is more of a spam menace than traditional malware, but gives search engines enough reason to block the site on accusations of distributing spam. Powered by the constantly updated threat defense feed, wordfence firewall stops you from getting hacked. File based caches have been compromised;
In affected versions the widgets editor introduced in wordpress 5.8 beta 1 has improper handling of html input in the custom html feature. A compromised plugin uses a filter to change the title; Wordfence scan leverages the same proprietary feed, alerting you quickly about security issues or if your site is compromised.

You could also use burp or your favorite scripting language for this request. Usually, the hacker is seeking access to data and obviously, the database is usually where it resides. The vulnerability is more of a spam menace than traditional malware, but gives search engines enough reason to block the site on accusations of distributing spam.

This leads to stored xss in the custom html widget. Database hacking is among the most important arts of the hacker. A hacker manages to change the title via an exploit;

It is also recommended on some forums to check for the existence of an option via code: You could also use burp or your favorite scripting language for this request. According to the wordpress codex (and my experiences developing with wp) note an important subtlety in the return value here:

Apr 26, 2018 · 4 min read. This leads to stored xss in the custom html widget. Usually, the hacker is seeking access to data and obviously, the database is usually where it resides.
A hacker has broken into redis/apc/memcached and modified the cache;
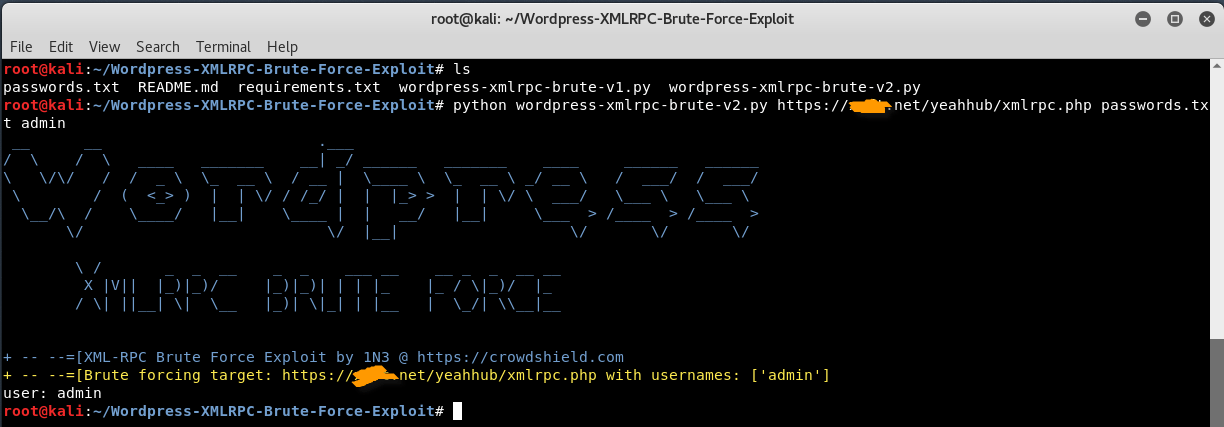
A compromised plugin uses a filter to change the title;

It is also recommended on some forums to check for the existence of an option via code:

Wordfence scan leverages the same proprietary feed, alerting you quickly about security issues or if your site is compromised.
This password guessing attack may also be faster, with the result being you can attempt more passwords.
Download at DOWN47.COM
0 Response to "Get Xmlrpc Wordpress Exploit Background"
Post a Comment